User & Terminal Management Software
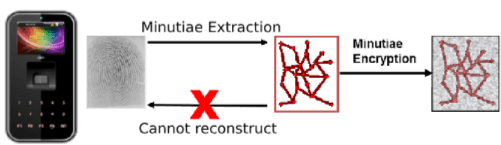
Authentication Types
Since all clients have different specific needs, we provide customized solutions to fulfill each and every requirements so that our clients can save time & money without compromising on security
Depending on type of terminals used, several authentications can be used to achieve the desired authentication mode per user
Terminal Features
All terminals are different in their respective ways. Depending on the client's requirement, proper advice & info are given while choosing the right terminal

Touch Screen
Touch screen gives additional information to the users while authenticating. Example User's name/ID and a user message can be read during authentication. Also this gives our client the ability to perform specific configuration right on the terminal itself (especially for cloud based system or centralized system where main software is OFF-site)
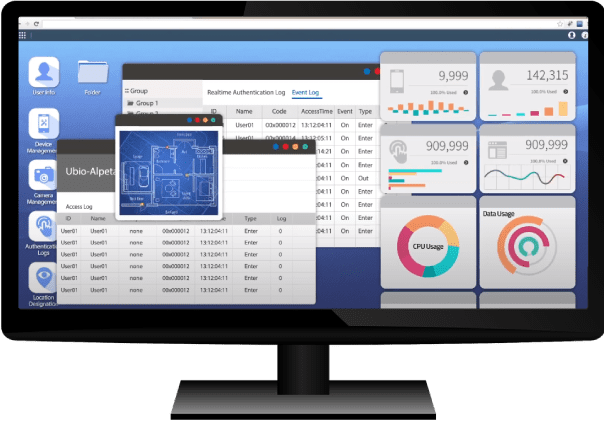
Control All your systems on one platform
Having all your system on one platform not only saves time but also gives you the power to manage easily without it being a hassle.